2024-05-10 23:22:55
After 11 months of being here, I decided to do a very small reflection.
When I first arrived, I didn't have any expectations or goals I'd like to achieve. Matter of fact, the main reason I left Twitter is because of all the bots that followed me and how I almost never got any real interaction.
Over time, things got a little rocky here and it seemed as though, personally, I wasn't going to be enjoying it any further at that time and contemplating shutting the instance down completely and just "disappearing".
However, several months on from that, I'm VERY glad I didn't. I like it here and I like having my "own little space" where nobody can tell me what I can and cannot discuss nor what I can and cannot see.
Something I've just recently realized though, is how important a good bit of you have become to me, personally and my Fedi experience would be very lacking without some of you here. What I didn't expect, was getting that same sentiment back when I discussed it with those few of you. I really appreciate knowing that for some of you, I have been consistently a "good" addition to your timelines and everyday online life.
Those types of comments and feelings they give me, keep me here and sane on those wilder days. To each and every one of you that have followed me for so long, through all the craziness, slight drama, wild opinions, and more, THANK YOU.
If I hadn't been almost universally accepted with such open arms and returned the same energy I try to put out, then I doubt I would still be here to this day.
I'm 11 months in and I think I'm ready to "give back" to those few folks that I consider friends and am on the cusps of creating something new and hopefully something good for Fedi as a whole.
I'm going to keep it very limited for specific reasons I'll lay out later. But, this is new ground for me and I have to figure some things out and hopefully not make too many missteps and learn some things along the way.
Thank you Fedi. I wouldn't be who I am right now, without you.
2024-04-04 08:25:51
"To focus on music venues as steps to be conquered on the way to a career is everything that is wrong with the commodification of art, especially in a time when that route is a slippery illusion. Let’s celebrate grassroots venues not as part of the infrastructure of an industry that’s nigh-on kaput, but for what they are – vital, beloved rooms where those onstage create an energy that, even if it’s only witnessed by 10, 20 people, lets us touch the electricity of music, and find a littl…
2024-03-30 21:58:50
My current take on the #xz situation, not having read the actual source backdoor commits yet (thanks a lot #Github for hiding the evidence at this point...) besides reading what others have written about it (cf. #rustlang for such central library dependencies would maybe (really big maybe) have made it a bit harder to push a backdoor like this because - if and only if the safety features are used idiomatically in an open source project - reasonably looking code is (a bit?) more limited in the sneaky behavior it could include. We should still very much use those languages over C/C for infrastructure code because the much larger class of unintentional bugs is significantly mitigated, but I believe (without data to back it up) that even such "bugdoor" type changes will be harder to execute. However, given the sophistication in this case, it may not have helped at all. The attacker(s) have shown to be clever enough.
6. Sandboxing library code may have helped - as the attacker(s) explicitly disabled e.g. landlock, that might already have had some impact. We should create better tooling to make it much easier to link to infrastructure libraries in a sandboxed way (although that will have performance implications in many cases).
7. Automatic reproducible builds verification would have mitigated this particular vector of backdoor distribution, and the Debian team seems to be using the reproducibility advances of the last decade to verify/rebuild the build servers. We should build library and infrastructure code in a fully reproducible manner *and* automatically verify it, e.g. with added transparency logs for both source and binary artefacts. In general, it does however not prevent this kind of supply chain attack that directly targets source code at the "leaf" projects in Git commits.
8. Verifying the real-life identity of contributors to open source projects is hard and a difficult trade-off. Something similar to the #Debian #OpenPGP #web-of-trust would potentially have mitigated this style of attack somewhat, but with a different trade-off. We might have to think much harder about trust in individual accounts, and for some projects requiring a link to a real-world country-issued ID document may be the right balance (for others it wouldn't work). That is neither an easy nor a quick path, though. Also note that sophisticated nation state attackers will probably not have a problem procuring "good" fake IDs. It might still raise the bar, though.
9. What happened here seems clearly criminal - at least under my IANAL naive understanding of EU criminal law. There was clear intent to cause harm, and that makes the specific method less important. The legal system should also be able to help in mitigating supply chain attacks; not in preventing them, but in making them more costly if attackers can be tracked down (this is difficult in itself, see point 8) and face risk of punishment after the fact.
H/T @… @… @… @… @…
2024-03-30 21:58:50
My current take on the #xz situation, not having read the actual source backdoor commits yet (thanks a lot #Github for hiding the evidence at this point...) besides reading what others have written about it (cf. #rustlang for such central library dependencies would maybe (really big maybe) have made it a bit harder to push a backdoor like this because - if and only if the safety features are used idiomatically in an open source project - reasonably looking code is (a bit?) more limited in the sneaky behavior it could include. We should still very much use those languages over C/C for infrastructure code because the much larger class of unintentional bugs is significantly mitigated, but I believe (without data to back it up) that even such "bugdoor" type changes will be harder to execute. However, given the sophistication in this case, it may not have helped at all. The attacker(s) have shown to be clever enough.
6. Sandboxing library code may have helped - as the attacker(s) explicitly disabled e.g. landlock, that might already have had some impact. We should create better tooling to make it much easier to link to infrastructure libraries in a sandboxed way (although that will have performance implications in many cases).
7. Automatic reproducible builds verification would have mitigated this particular vector of backdoor distribution, and the Debian team seems to be using the reproducibility advances of the last decade to verify/rebuild the build servers. We should build library and infrastructure code in a fully reproducible manner *and* automatically verify it, e.g. with added transparency logs for both source and binary artefacts. In general, it does however not prevent this kind of supply chain attack that directly targets source code at the "leaf" projects in Git commits.
8. Verifying the real-life identity of contributors to open source projects is hard and a difficult trade-off. Something similar to the #Debian #OpenPGP #web-of-trust would potentially have mitigated this style of attack somewhat, but with a different trade-off. We might have to think much harder about trust in individual accounts, and for some projects requiring a link to a real-world country-issued ID document may be the right balance (for others it wouldn't work). That is neither an easy nor a quick path, though. Also note that sophisticated nation state attackers will probably not have a problem procuring "good" fake IDs. It might still raise the bar, though.
9. What happened here seems clearly criminal - at least under my IANAL naive understanding of EU criminal law. There was clear intent to cause harm, and that makes the specific method less important. The legal system should also be able to help in mitigating supply chain attacks; not in preventing them, but in making them more costly if attackers can be tracked down (this is difficult in itself, see point 8) and face risk of punishment after the fact.
H/T @… @… @… @… @…
2024-02-28 08:34:12
This https://arxiv.org/abs/2307.08202 has been replaced.
initial toot: https://mastoxiv.page/@arXiv_ees…
2024-03-22 08:33:26
This https://arxiv.org/abs/2307.09478 has been replaced.
initial toot: https://mastoxiv.page/@arXiv_csGT_…
2024-02-12 19:59:37
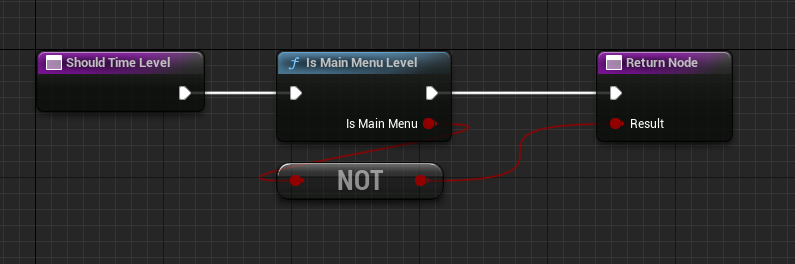
For today's developer humor, we can ask if it's the main menu level ... NOT. #GameDev